Splunk as a Product Enabler for Security
Published: June 2, 2023

In part one of this post, we talked about Product Thinking, what it is, and why it’s valuable to organizations. We also outlined a series of questions we normally consider when taking a product thinking approach. In part two we discussed what products Splunk might enable in the observability space. In this post, we’ll talk about Splunk as a product enabler for Security products and services – something key for any CISO to consider in the ongoing question to improve the security posture and security outlook for an organization.
Security & Log Archival
The ability to look back on log files that contain security-related information and to perform audits about who may have accessed services in a product can be critical when trying to understand what data or customers might be affected by a breach, or mistakenly granted access permissions to a service or asset. Even archiving logs for a period to enable investigations about how long defects or performance issues have been occurring can be extremely valued to a product team who is grappling with a long-running technical problem. With Splunk’s ability to leverage different types of storage, moving older content to less performant (and therefore cheaper storage) as it ages, log archiving is a natural capability that could be offered with Splunk via a product team. From a security perspective, Splunk can cryptographically sign blocks of logs to ensure they’re legitimate and haven’t been tampered with, and Splunk has best-in-class security settings across the product components to ensure your customer’s logs and metrics arrive safely and are as they appeared when they were first received by Splunk. This is another example of a service that could be offered to important applications via Splunk and could overlap with the observability and operational support services, above.
SIEM and Actionable Security Intelligence
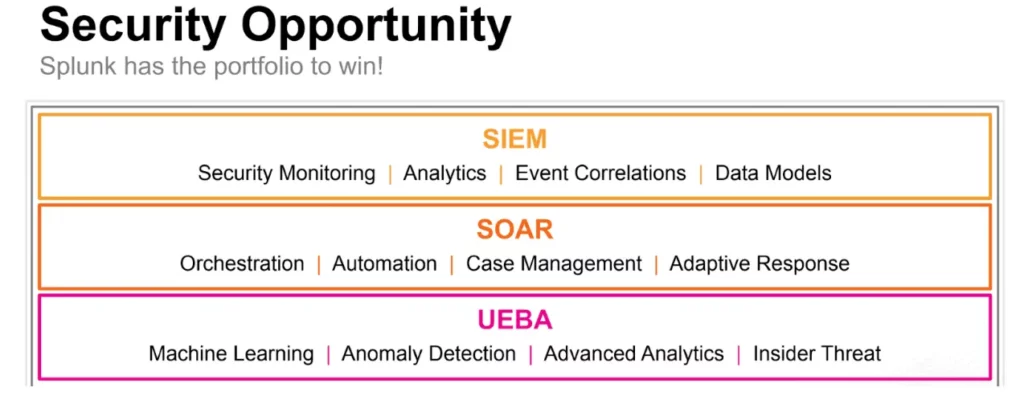
At the advanced end of Splunk usage, Splunk Enterprise Security (or even, initially, just a thoughtfully configured Splunk Enterprise instance that’s being used for the above activities), makes it possible to extend Security Information and Event Monitoring (SIEM) services to your organization. Perhaps offered to critical products and services within the company where security exposure is the highest business risk, or even extended to any product team that is authenticating users or performing business transactions, offering SIEM as a service can present real improvements in the overall security posture of a company. What’s extremely powerful about an implementation of Splunk by a thoughtful security group, is that it’s relatively easy to have timely and highly specific actionable intelligence alerts to your SOC. Perhaps initially focused on your boundary network security infrastructure, cloud configurations, and Identity Management Platforms (IDPs), a Splunk SIEM product can deliver a lot of peace of mind quickly, and be an effective way to identify security exposures in near real-time. UEBA is a Splunk component which can also make identifying questionable or outlying user behavior much easier, leveraging things like machine intelligence and pre-built use cases which can make monitoring applications and IDPs even more effective.
A product team offering SIEM as a service can focus on tuning and enabling use cases for security alerts triggering across multiple applications, making them performant, highly relevant, and actionable. A product team could also offer specific monitoring and alerting to certain applications, customized to their needs and risks. All this can be possible without having to force applications to change the format or even the content of their log files.
Splunk also comes with the benefits of more powerful product extensions such as SOAR, which can help to orchestrate automated activities when security events are detected. This might include connecting to other teams’ services to close down applications or components being threatened, automatically closing entry points in firewalls, and all sorts of additional automation which might extend your security product offering to your colleagues going forward.
The Splunk Security Stack
Here are the relevant Splunk components that might power the products we’ve talked about above.
In the next post, we’ll take a look at Splunk Cloud and how it might affect the products and services, and the approach to delivering them, that we’ve discussed in parts two and three of this blog series.
About the Authors
John Tobin has been working in software development for around 30 years, and has been working with Agile methods in the role of scrum master and product owner for product development teams for about half of that time. John has worked extensively with teams to deliver products and services in challenging and complex environments, delivering hundreds of thousands of dollars of business value over this time.
Doug Brown joined Solsys Corporation in 2013 as a Managing Consultant. Doug has tenures with large software organizations such as Oracle and Sun Microsystems leading professional services teams across North America. Doug has experience working with customers canvassing requirements, identifying critical solution architecture components. Success looks like great product teams delivering great value for their customers.



