API Monitoring: Your First Line of Defense Against Costly Security Breaches
Published: November 25, 2024

We keep hearing about API attacks leading to data loss and security breaches from large, even technology-based, corporations. For example, Dell recently lost 49 million customer order records to an API-based attack. It took three weeks before the attack stopped, and Dell didn’t even detect it. Like Dell, many organizations do not appear to be monitoring API traffic and reporting on those transactions in their Security Information and Event Management (SIEM) tools. So why not? Let’s take a deeper look at the issues.
API Security Attacks on the Rise
API Security is a complex issue with far-reaching consequences. It’s estimated that API attacks cost organizations $94 – $186 billion annually and account for more than 10% of cybersecurity issues. The average data breach now costs organizations $4.88 million, according to IBM. APIs are the largest attack surface for most organizations with more functionality being exposed via APIs than is even available in user-facing applications (websites, mobile apps, etc), making APIs one of the biggest security risks in the industry.
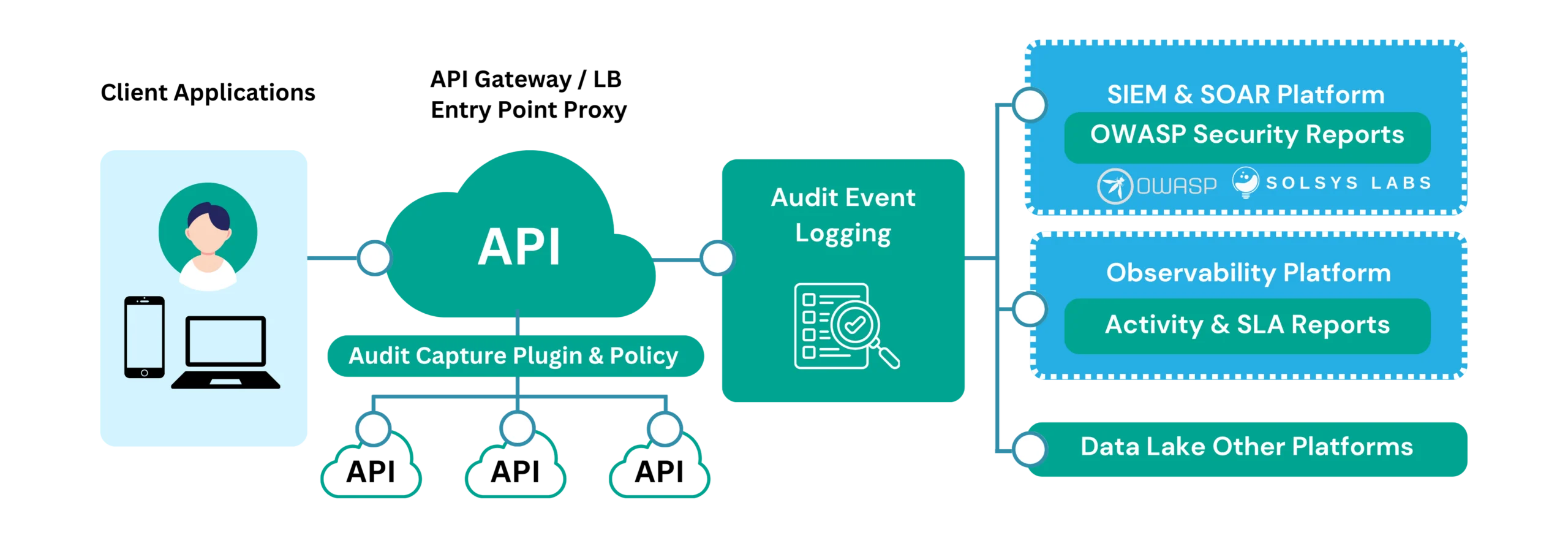
API monitoring – audit logging and capturing the right information about API transactions – can help provide visibility into API security and, with integration to a SIEM tool, capture and report on security exposures.
API Monitoring & Detection Challenges
There’s no doubt that spotting security issues in the noise of API traffic, where to log API events, what to log, and which use cases need investigation, is not a simple matter. API transactions can easily number in the millions per day, even in a mid-size company. API consumers and APIs themselves can often ‘behave badly’, causing errors and noise in the logging information which can trigger false positives.
Our Solsys Labs team here at Solsys have done a lot of work to figure out what to watch for in the ‘noise’ of your API traffic and how to recognize the fingerprints of an attack in the noise. A lot of it comes down to what you log, what capabilities your API Gateway or API implementations can support, and what systems, mechanisms, and API implementations your organization uses. Depending on these patterns, we’ve identified over 70 use cases that you could watch for in your API traffic. OWASP published an update to their API top 10 in 2023 and we’ve identified some use cases in the lab around those attacks that good API audit logging can help detect, among many others.
Our Approach Adapts to Your Investments
Our approach to API security is first to give this visibility to your API traffic. We adapt to your existing investments in API Gateways and SIEM tools to deliver an improved security posture and improved visibility.
API Monitoring and Visibility Has Many Benefits
This approach can be implemented without performance impacts to your APIs, and provide many varied and significant operational benefits to your IT teams (especially those responsible for delivering APIs). We have examples showing reducing the Mean Time To Resolution (MTTR) of API problems and issues by 95% by implementing good API monitoring, for example. Other operational and planning benefits exist too, such as governance reporting, traffic visualization, and many more. Visibility plays a key role in your API governance processes too.
This makes this API monitoring approach to API Security a high ROI proposition, and a great starting point to improving your API security posture.
How Solsys Can Help
Our team would be happy to show you some of these attacks and use case examples in our lab. Our experts are ready to help you with your API monitoring and security needs, please contact us to find out more about how we can work together to improve your API security and reduce risk.
John has over 25 years of experience working in software and technology, with professional services consulting firms and product companies, ranging from large enterprises to small firms. John currently works with Solsys to help clients with their API governance, API management, and API security problems. Having spent several years as a Product Owner of an API gateway and management platform for a large telecom client in Canada, John is using hard-learned lessons from the front lines of a high-performance and high-volume API platform to enable clients to improve how they deal with their API technology.



