15 Practices for Shielding Your APIs from Attack: #1 – APIs at Risk
Published: June 2, 2023
One of our customers, a leader in the Canadian Telecom Market, found that the need for a single business innovation service gateway was inhibiting business and imposing unrealistic business costs.
Their legacy API Gateway was missing many features, more over the code was outdated with no way to observe or measure traffic. This platform was performing the vital role of securing access to many business-critical APIs.
With planned significant increases in API usage on the horizon, driven by new business services to be offered by Media, Health, IoT, and 5G, Solsys was engaged to work with them to establish a next-generation API connectivity platform. With an eye towards quality and security, an essential part of this engagement has been to modernize security to address the API attack vector risk while retiring the legacy system.
APIs as an Attack Vector
Our client is right to be concerned about API attack vectors. They are large and increasing security concerns for corporations, at the same time that API usage is increasing and becoming critical to strategic business operations and for enabling innovation with partners and cloud services. According to Forbes and as predicted by Gartner, 2022 saw a large spike in API security threats. The API attack vector is still a high-risk issue in corporations, and 2023 kicked off with T-Mobile revealing the theft of the personal data of 37 million of their customers from an exposed API endpoint in the last few months.
Our Security Journey & Lessons Learned
In our multi-year journey with our client, we have significantly improved their security posture, provided full observability and security audit events, retired their legacy high-risk API platform, and delivered many API management capabilities to enable innovation and faster time-to-market.
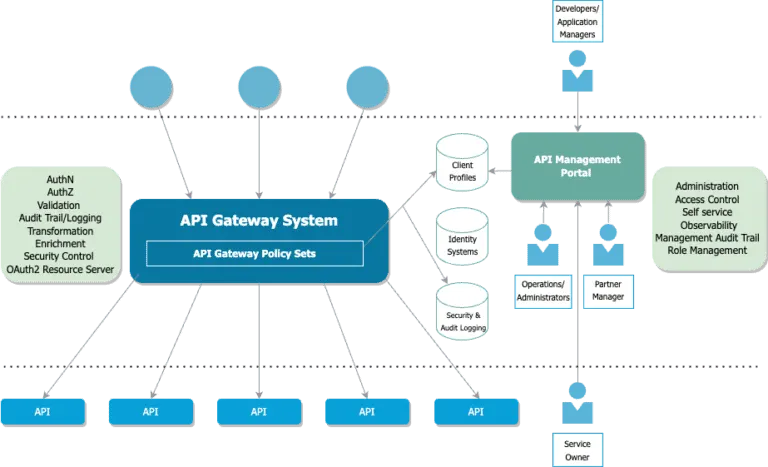
In this series of posts, we will share the practices of our product development teams in building and securing APIs and implementing a defence strategy with this customer to protect and enable the use of their API assets. We will discuss the practices (activities, approaches, tools, platforms, systems, ideas, architecture, and designs) that have enabled our development teams to securely develop this secure API platform product with our Canadian client and how we continue to ensure that this software remains secure. While the title of this post relates to API security and this journey, the practices discussed in this series apply to all software development.
Later in the series, we will discuss specific security risks and how these working practices are applied to help avoid them. We will be reviewing the OWASP top 10 security risks, and explaining how the practices we have outlined help to avoid these problems.



